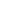Securing Mobile Apps: Best Practices for Developers

It’s essential to pay attention to mobile app security best practices UK while creating a mobile application. Securing mobile apps: best practices for developers can be the game changer. Hackers are always looking for new methods to take advantage of security flaws, and data breaches may have a bad effect on your business’s reputation and customer experience. You should launch a successful mobile app that protects the data of both your customers and the organisation.
For that, the developer needs to adhere to the mobile app security best practices. To minimise security flaws and protect your mobile application from security breaches, check out the following top security frameworks for mobile apps. With the help of these points make your app secure but before that know what is app security and the types of threats.
What Is Security for Mobile Apps?
Security in the context of mobile apps refers to a certain set of guidelines, norms, and procedures. Certain of those are universal and may uses with any kind of device or application. Some, which highlight their special qualities—like the inclusion of cameras, a variety of sensors, GPS, etc.—are made exclusively for mobile devices. The purpose of mobile app encryption methods UK is to guard against dangers like data theft and unauthorised access to both software and hardware.Typical Mobile Security Risk Types
Vulnerabilities that remain in the code of an operating system or mobile application are passive threats. They might be ports of entry for malevolent hackers to carry out their attacks. An application poses a danger, for instance, if it employs an antiquated security standard or transmits data without encryption.One of a hacker’s many tools is active threats. A variety of tools are available to deliberately compromise mobile security and steal data, including malware, spyware, viruses, phishing websites, and scripts. They may hide on machines and divulge personal information for months, or they may pose as innocuous software or webpages.
Best Practices to Secure Mobile App Development UK
-
Use a certificate for code-signing.
-
Employ Advanced Authentication

The usage of two-factor authentication in apps is becoming essential. Simply said, authentication is the use of passwords and other unique identifiers as entrance barriers. Sure, a lot of this is dependent on the end users of your service, but you can, as a developer, urge users to take authentication more seriously. It is possible to create applications that can only take strong passwords that are alphanumeric and need to be changed every three or six months. Static password and dynamic one-time token (OTP) combinations known as multi-factor authentication are becoming more and more popular. Mobile app authentication techniques UK like fingerprints and retina scans can also be utilised in the event of apps that are too sensitive.
-
Using Current Techniques for Encryption
-
Regularly testing and observing mobile apps
Start keeping an eye on user activity inside the app’s statistics after its initial release. When new features arrive or problems arise, reevaluate the metrics and make any necessary adjustments. Add something additional if the user experience does not improve after making a change. Maintaining a continuous testing and improvement procedure will contribute to your company’s success. Mobile app security compliance for UK developers such as encryption and offline data backups, to ensure that data remains retrievable in the event of an application penetration.
-
Protecting the App Backend
-
Install Tamper Detector
-
Cut Down on Sensitive Data Storage
These are the top practices that DigitilizeWeb follows. So, consider these tips as well experimented by the team of app developers. Now let’s get into the advantages, what are things you save yourself to conduct proper security practices.
Advantages of Techniques for Securing Mobile Apps Against Hacking
-
Increased security for financial data.
-
Private messages
-
Defence against the theft of hardware
What can DigitilizeWeb do for you?

It is crucial to ensure Mobile app security best practices UK are followed. For this reason, it needs to be delegated to knowledgeable engineers with the necessary training and testing equipment. These professionals are available at DigitilizeWeb, where they provide a variety of mobile app development services and collaborate in well-experienced teams.
We maintain the highest levels of quality and security, thorough testing as per UK regulations on mobile app security. In one word, we are providing the whole development life cycle for your app.
So, if you want to know more about our services, and our offers then you can contact us. For more follow us on LinkedIn.